A lot is going on in the network monitoring arena, with network systems becoming more complex, Software Defined Network (SDN) slowly coming into the picture and malware speeding up the pace. Solutions are adapting to hybrid cloud to fill the visibility gaps, using Artificial Intelligence (AI) as their integral part as well as coping with constant and dramatic bandwidth growth. In this technology shifting period, do you have an outright and complete network monitoring strategy? Are you sure?
Why do most network monitoring strategies fail?
Network monitoring is a set of mechanisms and tools that provide network administrators with visibility into network traffic, the past and current state of the network, network performance, the health and availability of infrastructure and services, as well as security breaches that occur within the network. Together, these mechanisms and tools enable administrators to proactively and quickly respond to any issues or anomalies, thus maintaining smooth network and business operations.
Common practice in
To put things straight – while checking availability and performance of infrastructure and services is mandatory and irreplaceable for networks of any size, in today’s complex environments device-centric monitoring with a simple and basic set of (usually SNMP) performance counters is not sufficient to ensure visibility, availability and reliability of network and critical business services, as it leaves network traffic completely unmanaged and unknown.
Can you really be sure that everything is going well just because no one is complaining? Do you just see the conversation participants but do not hear the conversation? This silence can come at a high cost. Especially when it comes to security issues which are usually a keep-low-profile type of conversation. And this is exactly where a lot of network monitoring strategies simply – fail.
Let’s talk about network traffic monitoring tools
So, how about joining the conversation? We need to get back to basics. Techniques of network performance monitoring can be either active or passive. While passive monitoring reads data from the network without affecting the traffic, active monitoring modifies or injects traffic into the network.
Active monitoring, such as
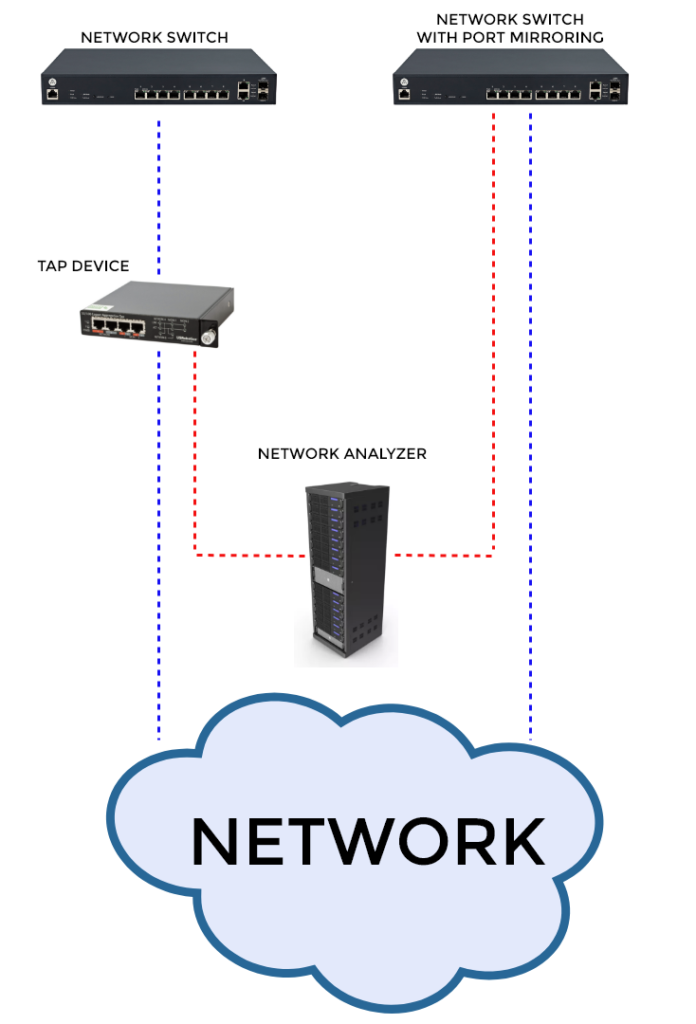
Passive network performance monitoring does not introduce overhead in the network, is less resource-intensive and enables analysis of larger volumes of data. Depending on the amount of details of the monitored network traffic, several approaches arise, each with its trade-offs. Passive network performance monitoring can be divided into two processes: traffic duplication and traffic analysis. The two most common ways for traffic duplication include port mirroring and inline TAP device positioning.
On the other hand, flow analysis – stripping the payload from the data – gives detailed insight into network traffic much faster, with less stored data and privacy concerns. While multiple vendor protocols exist, all conforming to a basic set of details such as source and destination IP addresses, communication ports, protocols and transferred traffic in bytes and packets, the most flexible is IPFIX developed by IETF which enables vendors to export a much larger, proprietary set of parameters. This allows enrichment of exported data and analysis of traffic all the way to the upper levels of the OSI model. This further enables analysis of special types of traffic (DNS, DHCP, HTTP, etc.) and insight into both network and application performance.
The availability of flow statistics for your entire network traffic will help you streamline network optimizations, troubleshoot and enhance security by detecting traffic anomalies that are beyond reach to perimeter systems.
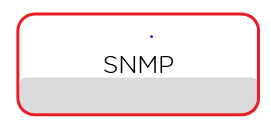
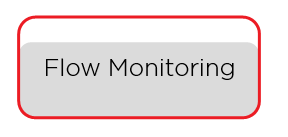

- Basic performance counters information
- How many packets, bytes
- Device/interface centric
- Who talked to whom?
- Which ports, protocols, data amount and type
- Conversation centric
- Detailed insight into network packets
- Time and resource consuming
- Content centric
While the solutions out there are numerous, our number one choice in delivering network visibility and diagnostics are Flowmon products. They are scalable, robust and offer possibilities of integration that, combined with our infrastructure monitoring, helped us create comprehensive monitoring solutions for our Customers.
Three perspectives you need to include in your network monitoring strategy
The wise and experienced understand two statements: use the right tool for the right job, and there is no “one solution to rule them all”. There is a lot to think about when it comes to deciding on strategy. Solutions shall depend on your size, cloud or on-premise network model, as well as price. You will need to take scalability into consideration as you are going to grow. Multi-vendor support and ease of implementation and configuration is something that is going to make a difference also.
Here at Inceptum, we help our customers and we can help you in getting in the game and making well-informed decisions. Most of all, your existing ecosystem is going to dictate the possibilities and necessities of integrations – which is a crucial question. Having an educated professional is a must have, and this is where our experts can leverage the entire implementation and integration process. This is what we know how to do and love doing it. Nonetheless, your strategy must cover all perspectives – security, infrastructure and network traffic. Get the most from your data for your business. In the end, it’s a data era, right?